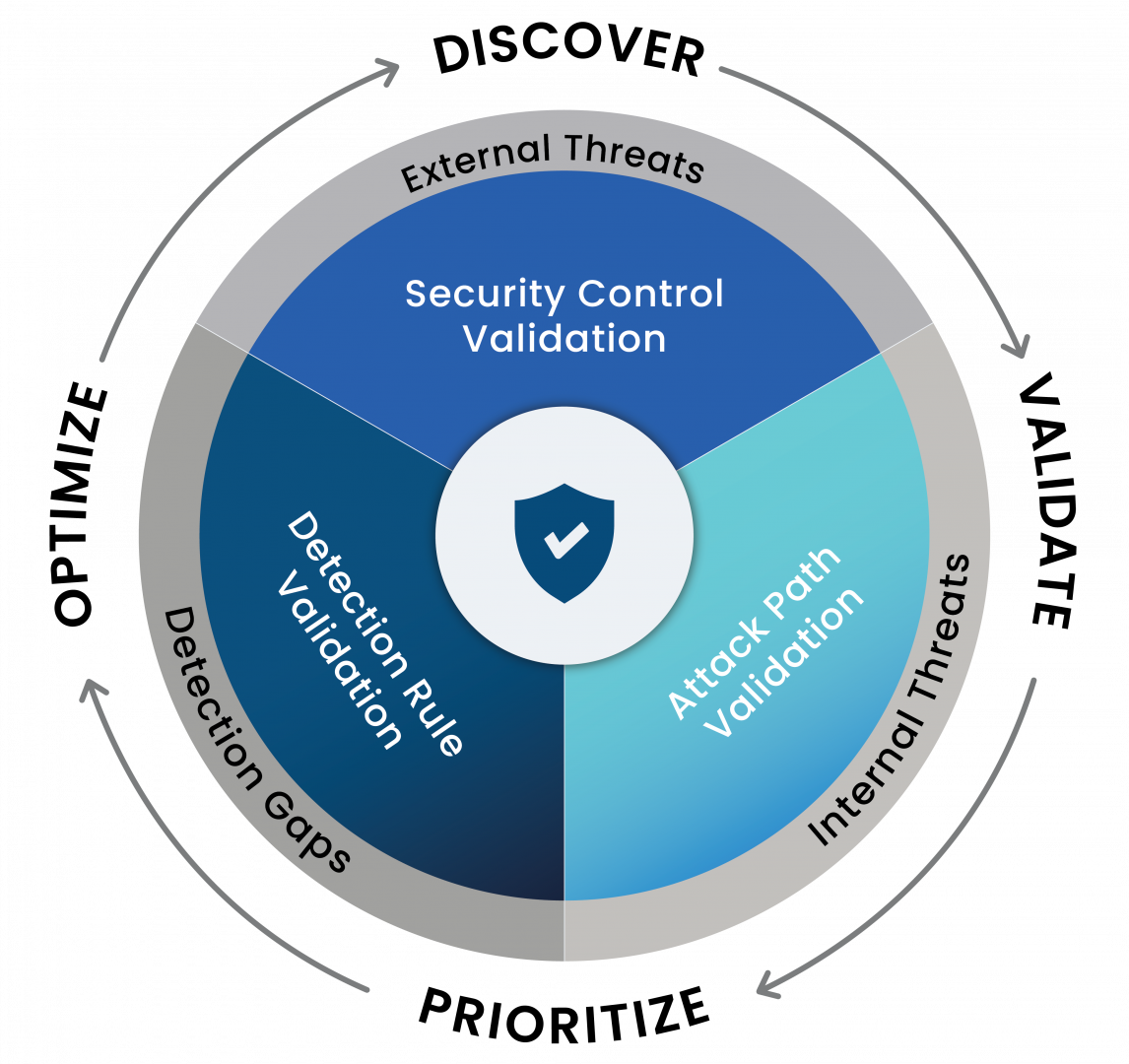
Security Control Validation
The evaluation and verification of an organization's security control effectiveness can be achieved through continuous attack simulations and security tool testing. This process helps minimize vulnerabilities and enhances confidence in the organization's cybersecurity defenses.
Our platform serves as a tool to test the effectiveness of your organization's cybersecurity systems by simulating attacks, known as Breach & Attack Simulations. These simulations test the infiltration of your network, email, and web applications, as well as the exfiltration of endpoints and data. The platform is capable of operating both on the cloud and on-premise.
Every year, organizations invest heavily in various cybersecurity devices and platforms. However, how can you be sure of their effectiveness in defense? How do you identify the areas that need improvement to prevent vulnerabilities to threats? Therefore, it's essential to have a tool that tests the efficiency of your current cybersecurity systems. Additionally, the platform from Picus Security helps organizations plan future investments by prioritizing which areas need immediate attention and which can be addressed later.
Key features
✓ An extensive library of 4,000+ threats consisting of 20,000+ actions, updated daily
✓ Simulates attacks instantly or per a predefined schedule
✓ Individually customizable threats and attack scenarios
✓ Validates network security, SIEM & EDR tools
✓ Over 70K+ prevention signatures and detection rules
✓ Maps results to MITRE ATT&CK
✓ Executive dashboards and reports
✓ Cloud-native SaaS Platform
✓ Supports Windows
Improves Your Security Posture

Tests security controls
continuously, 24/7
Identifies threat prevention and detection weaknesses by assessing the effectiveness of your security tools via continuously scheduled simulations.

Validates preparedness
against the latest threats
With a rich threat library, updated daily by offensive security experts, We test your defense against current and emerging attack techniques.

Optimizes prevention and
detection capabilities
To achieve optimal protection from your security tools, Picus supplies easy-to-apply prevention signatures and detection rules.

Operationalizes MITRE ATT&CK
We maps assessment results to the MITRE ATT&CK Framework, enabling you to visualize threat coverage and
prioritize mitigation of gaps.

Evidences the value of investments
Supplying real-time metrics, including an overall security score for your organization, Picus helps you to measure performance and prove value.

Improves SOC efficiency and effectiveness
We automate manual assessment and engineering processes to reduce fatigue and help your security teams work together more collaboratively.
Our company has prepared the Red Report 2024, a detailed analysis of the evolving cyber threat landscape. The report analyzes over 600,000 malware samples to identify the strategies that pose the highest risks to organizations. Key sections of the report include:
- Analysis of the top 10 MITRE ATT&CK techniques.
- Insights into how adversary behaviors have changed over the past year.
- Practical recommendations for strengthening your cybersecurity defenses.
Fill out the form to download the report here.
Contact our expert
By submitting, I agree to the processing and international transfer of my personal data by DataOne Asia as described in the Private Policy.
